Reverse Engineering Android Apps
Any Android app that makes HTTPS API requests (in this case to the myVAILLANT API), can be reverse engineered with an Android device and a laptop / PC that runs ADB. Both need to be on the same network. Creating a hotspot from the Android device also works.
- Run mitmproxy on your laptop, for example in Docker:
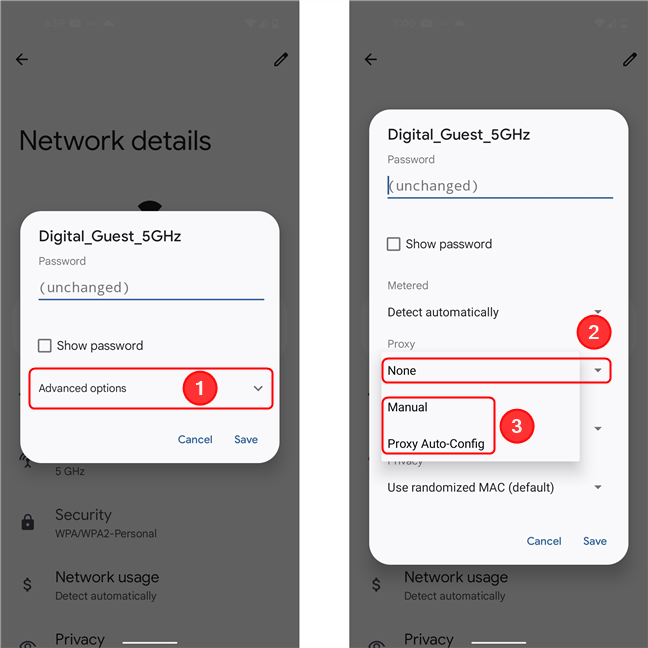
- In your Android WI-FI settings (see screenshot below) set a manual proxy to the IP of the device running mitmproxy on port 8080.
Add a bypass for
identity.vaillant-group.com1 - Visit mitm.it on your Android device, download the CA cert & install it through the settings app
- Install ADB on your laptop and connect your Android device to USB in debug mode
- Look for the myVAILLANT APK online and download it
- Install & run apk-mitm on the APK and install it with adb:
You should see all API calls in mitmproxy's web interface on http://127.0.0.1:8081 now.
Note
If you can't log in with SSO because of a certificate error, make sure you added the exception to the proxy settings.
If you can log in, but the app reports an error, the unpinning didn't work. You can try MagiskTrustUserCertson if you have a rooted Android device.
-
The single-sign on gets handled in your browser, which uses certificate pinning as an added security measure ↩